The need for effective fraud detection models has turned out to be of great importance in the ever-evolving landscape of digital transactions. Whether you're a data scientist trying to decorate your toolkit or a business owner aiming to make stronger defenses against monetary threats, join us in exploring the tools and strategies that safeguard against financial threats in the present day dynamic environment. This blog is the place for you.
As we navigate this landscape, we unveil the energy of Nected—a low-code/no-code rule engine and workflow automation platform designed to empower product, increase, and tech teams. Nected enables the short release of dynamic workflows, facilitates experimentation simply, and helps faster iterations—all with minimal attempt.
Embark on a journey with us as we explore the transformative panorama of fraud detection fashions, with Nected.
Lets us go through some important definitions that will heighten your knowledge on our blog’s context
What is fraud detection act?
In the U.S Fraud detection and prevention are on the whole ruled via a mixture of federal and state legal guidelines, in addition to industry-unique guidelines. For instance, the U.S. Has legal guidelines which include the False Claims Act, the Securities Exchange Act, and the Sarbanes-Oxley Act, which deal with numerous factors of fraud, inclusive of monetary fraud, securities fraud, and healthcare fraud. Additionally, regulatory bodies just like the Federal Trade Commission (FTC) and the Securities and Exchange Commission (SEC) play a large role in enforcing laws associated with fraud detection and prevention.
What is an Anomaly Detection Data Model?
An anomaly detection statistics model is a machine mastering version that identifies unusual or bizarre behavior in data, which may additionally suggest fraudulent hobby or different anomalies. Anomaly detection may be executed in unsupervised mode, which finds outliers inside the statistics without requiring a target, or in supervised mode, which makes use of categorized facts to train the model. Anomaly detection may be utilized in numerous programs, along with community visitors monitoring, cybersecurity, coverage fraud, or credit card fraud. Anomaly detection fashions can be constructed the use of various algorithms, inclusive of Isolation Forest, One Class SVM, and Local Outlier Factor(LOF).
The Below Image represents how Data Sets interact with Models and derive results
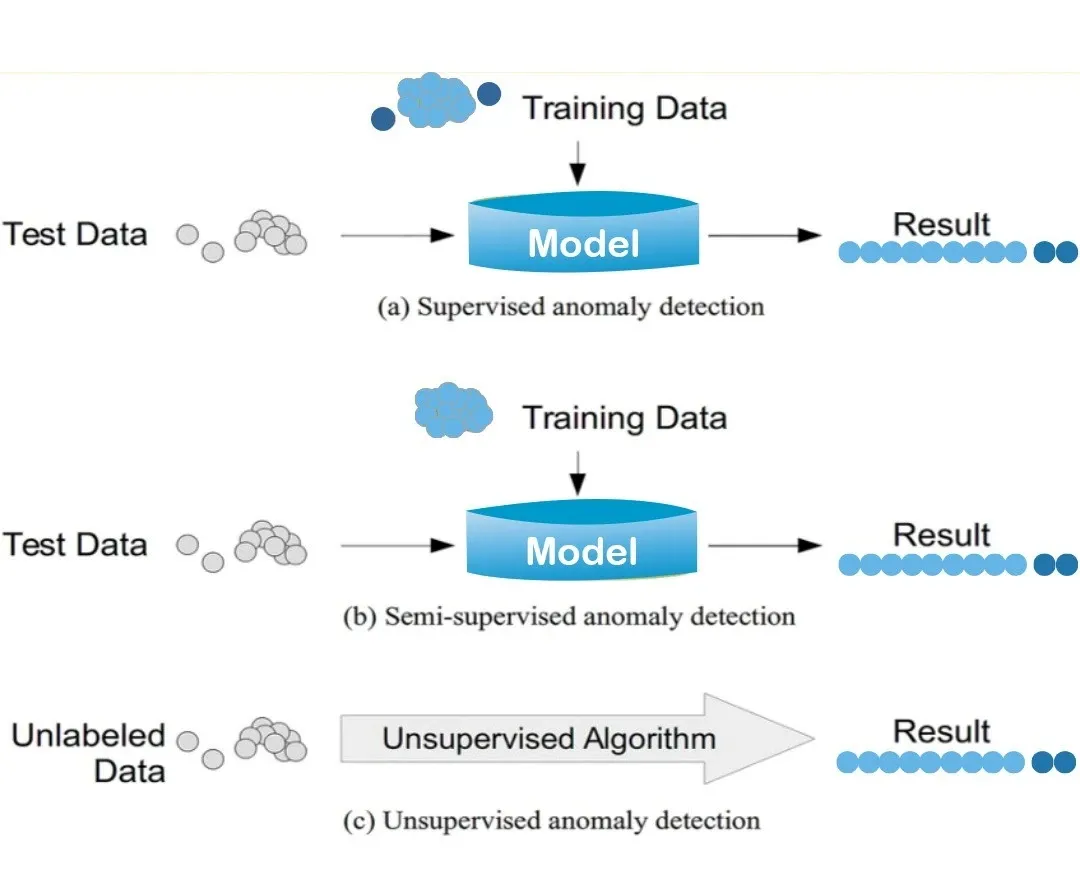
What is a fraud detection model?
A fraud detection model is a set of rules designed to discover and prevent fraudulent practices by means of reading patterns and anomalies in datasets. Let us start with an early instance of such a model “Address Verification System (AVS)”which was utilized in credit card transactions throughout the 1990s. AVS checked the billing cope with against the company's information to discover capability fraud. Another ancient method worried anomaly detection to become aware of unusual patterns in e-trade transactions, which include more than one transactions in a short time. Today, fraud detection fashions leverage advanced technology like machine learning to combat evolving fraudulent tactics.
Fraud Detection Model Example:
An example of a fraud detection model in use is the real-time monitoring of economic transactions used by banks and financial institutions. These companies utilize machine learning algorithms to analyze transaction information in real-time, identifying patterns and anomalies that could indicate fraudulent activity. By constantly tracking transactions as they occur, the device can readily flag and check out fraudulent conduct, supporting to save monetary losses and shield clients from fraudulent activities. This real-time approach to fraud detection is critical in today's digital surroundings, where the speed and accuracy of figuring out and responding to fraudulent transaction is of paramount importance.
Read Also: Which Is the Best Fraud Detection Technique In 2024?
Classifications of Fraud Detection Model
As we progress in this blog, let's delve into understanding the primary player in modern fraud detection landscape: fraud detection machine Learning model. But, first we should see the image below which provides an overview of fraud detection models, categorized into two groups — Machine Learning and Traditional.
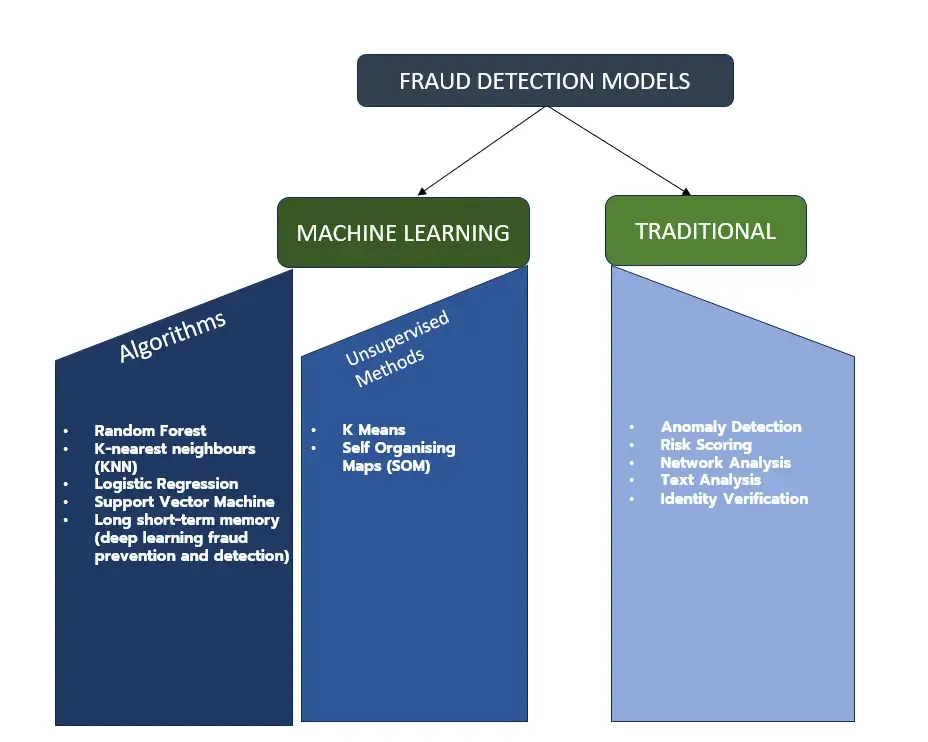
We have summarized the mentioned items in below table and defined them feel free to book a demo with us with any questions you have , We would be delighted to interact with you.
What are the challenges associated with implementing Machine Learning Models For Fraud Detection ?
- Integrating fraud detection ml models can be complex , especially for businesses with limited technical expertise .
- Concerns about data privacy and security are heightened when machine learning models are deployed for handling sensitive information .
- Dynamic fraud tactics require models that can adapt in real time .Businesses need flexibility to modify rules rapidly .
- Efficient fraud detection ml models requires seamless integration with existing databases and systems .
How to Monitor a Fraud Detection Model In Production?
Monitoring a fraud detection model in production is essential for maintaining its effectiveness. Key aspects to focus on include:
- Performance Metrics: Track accuracy, precision, recall, and F1 score to ensure balanced performance.
- Real-time Alerts: Implement a system for real-time alerts on suspected fraudulent activities.
- Model Drift Detection: Regularly check for model drift and update the model to adapt to new fraud patterns.
- Data Quality Checks: Ensure input data is clean and consistent to maintain accurate predictions.
- User Feedback Integration: Incorporate feedback from fraud analysts to improve model accuracy.
By focusing on these areas, you can maintain a robust fraud detection system that adapts to evolving threats.
How Nected is Overcoming Challenges in Fraud Detection ML Models?
User-Friendly Environment:
Nected's low-code/no-code interface empowers teams with varying technical understanding to implement powerful fraud detection workflows results easily.
Data Security Prioritization:
Built on industry quality-practices, Nected guarantees robust information protection. Optional on-premise installations provide organizations to be aligned with prescribed security standards.
Real-time Adaptation and Flexibility:
Nected's intuitive platform allows corporations to alter rules easily, ensuring adaptability to evolving fraud procedures in real-time.
Seamless Integration:
Nected shines in its ability to seamlessly combine with numerous databases, imparting flexibility and customization options for an easy integration procedure.
In navigating the demanding situations of adopting machine learning and getting to know fraud detection, Nected not only gives solutions but transforms these demanding situations into possibilities for businesses to solidify their security features.
Read Also: Fraud Detection in Data Mining: Techniques, & Data Insights
Scenario: Ensuring Integrity in Healthcare Billing with Nected
Picture a scenario where a healthcare issuer leverages Nected's distinct characteristic to determine billing quantities primarily based on the quantity of affected person consultations conducted with the aid of each scientific expert. The accuracy of mentioned consultations is crucial for honest compensation and obvious economic practices.
Ideal Operation
In ordinary operations, healthcare professionals are liable for appropriately documenting the wide variety of patient consultations they carry out. Nected's predefined situations align with the billing hints, developing a structured framework for calculating compensation based totally on these consultations.
Potential Fraudulent Activity
Now, consider a state of affairs where a healthcare provider tries to govern the billing gadget for monetary benefit. A clinical professional, looking for to increase their billing amounts, manipulates the stated range of patient consultations by using creating fictitious entries within the system.
Nected’s Response
Nected's superior fraud detection capabilities come into play as soon as the medical professional manipulates the stated number of patient consultations, deviating from the predefined situations. Nected expectedly detects this suspicious activity, recognizing the deviation from the hooked up norms.
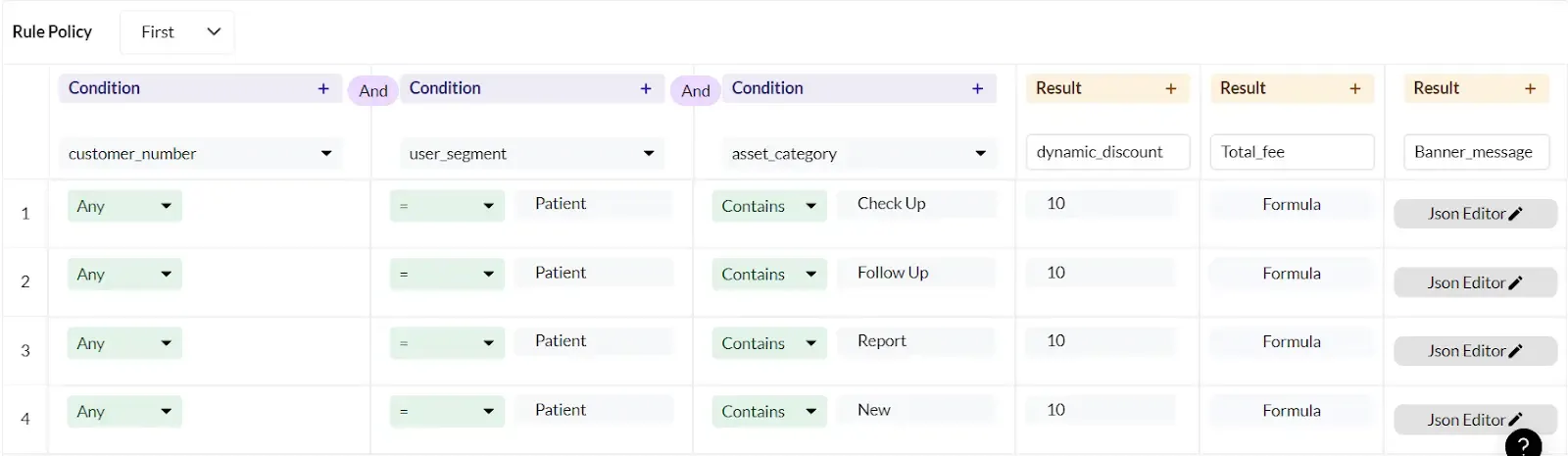
The above image shows a combination of conditions that needs to qualify for billing. Any customer number who is a patient if comes for either check up, follow up, report is getting a discount. There must be a database where new customers are registered and that database gets integrated with Nected . So manual intervention is not possible that omits the chances of fraud.
Automatic authorization Rejection:
Upon detecting the fraudulent activity, Nected takes on the spot action. The software marks the pastime as no longer authorized based on the predefined situations. This automated response ensures that any try and manipulate the billing device is identified and flagged in real-time.
The above can be considered as a fraud detection model demo by Nected. Try Nected’s Fraud Detection solution and safeguard your business!
Conclusion
From important definitions to exploring classifications and challenges, Nected emerges as the solution-driven ally. In scenario-based examples, we witnessed its efficacy in actual-time fraud detection throughout industries.As we pave the way to a more secure digital future, don't forget Nected no longer just as a tool however as a strategic companion in the ongoing war in opposition to fraud.
Book a demo with us, and permit Nected to revolutionize your approach to fraud detection. Together, let's embark on a journey toward a stable and resilient future.
FAQ
Q1. What legal frameworks govern fraud detection within the United States?
In the U.S., fraud detection and prevention are regulated by means of federal and state guidelines, including acts like the False Claims Act, Securities Exchange Act, and Sarbanes-Oxley Act. Regulatory bodies which includes the Federal Trade Commission (FTC) and Securities and Exchange Commission (SEC) play vital roles in imposing those legal guidelines.
Q2. How does Nected address the demanding situations of implementing machine learning models for fraud detection?
Nected addresses complexities with a user-friendly environment, prioritizes data protection, ensures real-time adaptability, and seamlessly integrates with databases. It turns demanding situations into opportunities, imparting a strong solution for companies navigating the landscape of fraud detection.
Q3. What are the primary machine learning algorithms used in fraud detection ml models?
Fraud detection ml models utilize various machine learning algorithms, including Random Forest, K-Nearest Neighbors (KNN), Logistic Regression, Support Vector Machine (SVM), and Long Short Term Memory (LSTM). Unsupervised methods like K-Means and Self Organizing Maps (SOM) are also employed to identify anomalies.
Q4. What are the key benefits of using machine learning models for fraud detection?
Machine learning models for fraud detection can analyze vast amounts of data quickly and accurately, identify complex patterns that humans might miss, adapt to new types of fraud through continuous learning, and provide real-time fraud detection, thereby reducing financial losses and enhancing security measures.
Q5. How can businesses ensure the effectiveness of their fraud detection models?
Businesses can ensure the effectiveness of their fraud detection models by regularly updating and retraining their models with new data, monitoring the performance of models in production, using a combination of supervised and unsupervised learning techniques, and integrating the models with existing systems for seamless operation. Additionally, implementing feedback loops to capture and correct false positives and negatives can improve model accuracy over time.
.svg)



.svg)



.png)




.jpg)

.svg)










