In the fast-paced world of business, keeping our operations safe from fraud is a big deal. Fraud detection is like the superhero shield that protects us from deceptive tricks, making sure everything runs smoothly. One powerful system in this fight is rules-based fraud detection – a smart way of using predefined rules to catch those sneaky fraudsters.
What's rules-based fraud detection? It's like having a set of watchful eyes that follow specific rules to spot anything fishy. If something looks off, these rules trigger an alert, letting businesses act quickly to stop potential fraud. Now, imagine having a tool that not only understands these rules but also lets you customize them as per your business needs. That's where Nected steps in – our superhero solution for rules-based fraud detection.
So, as we take this journey into the world of fraud detection, we'll see how rules-based detection is a game-changer. And with Nected by our side, it's not just about keeping things safe; it's about staying one step ahead in the battle against fraud. Let's explore the practical side of rules-based fraud detection with Nected – because securing your business should be both effective and easy.
Understanding Fraud Detection

Fraud detection stands as a guard guarding the financial integrity and reputation of businesses in today's dynamic digital landscape. At its core, it involves the identification and prevention of deceptive practices that can endanger financial transactions, compromise sensitive data, and destroy trust.
The significance of fraud detection cannot be overstated. In an era dominated by online transactions and interconnected systems, businesses face a lot of risks from increasingly sophisticated fraudulent activities. From identity theft to payment fraud, the threats are diverse and ever-evolving.
Challenges in the realm of fraud detection are multifaceted. Fraudsters constantly innovate, finding new ways to exploit vulnerabilities and bypass traditional security measures. The sheer volume and speed of digital transactions make it challenging to manually scrutinize each activity, necessitating advanced technological solutions.
Technology emerges as the backbone in the battle against fraud. Advanced algorithms, machine learning, and artificial intelligence play pivotal roles in analyzing vast datasets in real-time. They can discern patterns, anomalies, and subtle indicators of potential fraud that might elude human detection. This technological synergy empowers businesses to fortify their defenses and stay one step ahead of fraudulent activities.
In essence, fraud detection is not just a reactive mechanism to identify ongoing fraud but a proactive strategy that utilizes technology to anticipate and prevent fraudulent activities before they inflict damage. It's a critical component of risk management, enabling businesses to foster trust, protect assets, and uphold their financial well-being in an increasingly complex digital ecosystem.
Types of Fraud Detection

Fraud, like a chameleon, adapts its colors to various schemes, making it imperative to employ diverse and specialized approaches for detection. Let's delve into the distinct types of fraud and understand why tailor-made strategies are essential:
1. Identity Theft:
- It involves the unauthorized acquisition and use of someone's personal information, often for financial gain.
- Robust identity verification mechanisms, biometric authentication, and continuous monitoring are crucial to spot unusual patterns in personal data usage.
2. Payment Fraud:
- Payment fraud encompasses illicit activities related to financial transactions, including credit card fraud, wire fraud, and fraudulent fund transfers.
- Real-time transaction monitoring, anomaly detection algorithms, and two-factor authentication are essential tools to combat payment fraud effectively.
3. Insurance Fraud:
- Individuals or entities manipulate insurance claims to gain undeserved benefits or compensation.
- Data analytics, pattern recognition, and thorough claims investigation can expose inconsistencies and identify potential instances of insurance fraud.
4. Cybersecurity Fraud:
- Cybersecurity fraud involves attacks on digital systems, including phishing, ransomware, and malware.
- Advanced firewalls, intrusion detection systems, and regular security audits are essential components to safeguard against cybersecurity fraud.
5. Employee Fraud:
- Internal actors within an organization engage in fraudulent activities for personal gain, such as embezzlement or misappropriation of funds.
- Implementing strict internal controls, conducting regular audits, and fostering a culture of transparency and integrity can deter and detect employee fraud.
Each type of fraud demands a variable approach, recognizing the unique characteristics and red flags associated with it. A comprehensive fraud detection strategy incorporates a mix of advanced technologies, vigilant monitoring, and proactive measures to stay ahead of the ever-evolving landscape of fraudulent activities.
Create fraud alerts within minutes with Nected. Signup Now!
Rules-Based Fraud Detection
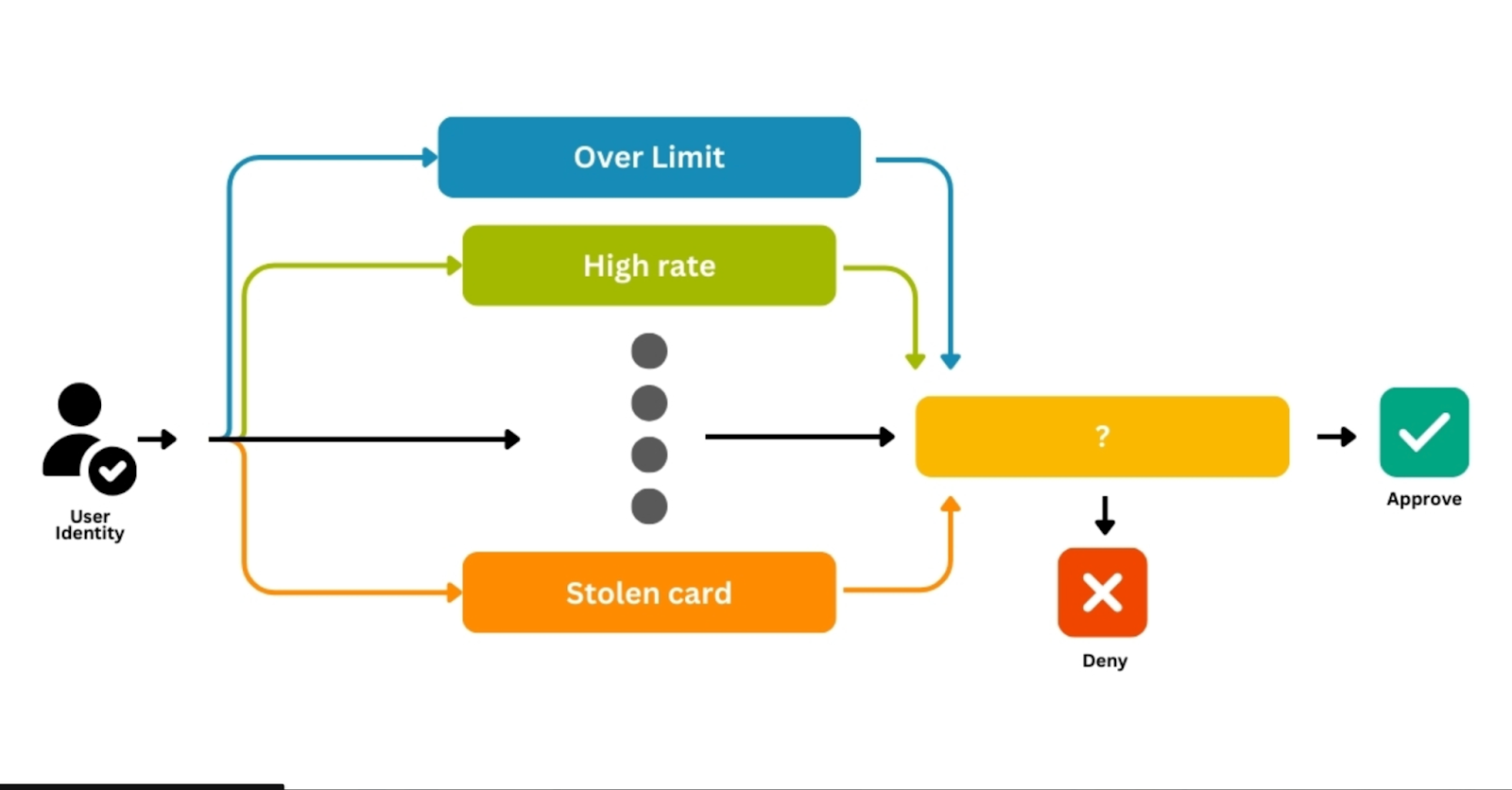
In the domain of fraud detection, rules-based approaches stand out as practical guardians. This section dives into the core of this strategy, unfolding its details, strengths, and considerations.
Rules-based approach is essentially a proactive defense system. It relies on predefined rules and criteria to scan transactions for anomalies resembling known fraud patterns.
Methodology Breakdown
- Rule Creation: Experts create rules based on insights into historical fraud patterns, transaction behaviors, and red flags.
- Thresholds: Parameters and thresholds are set as benchmarks to evaluate transactions, triggering alerts when necessary.
- Real-Time Application: The beauty lies in real-time application – rules are promptly applied as transactions occur, allowing immediate identification of potential fraud.
Benefits of Rules-Based Fraud Detection
- Accuracy: Rules offer precision, tailored to detect specific patterns and ensure accuracy in identifying potential fraud.
- Real-Time Detection: In the fast-paced financial landscape, rules-based systems shine with real-time operation, swiftly detecting and preventing fraudulent transactions.
- Customization: Flexibility is a key asset. Rules can be easily customized or new rules added to adapt to emerging threats.
- Clear Identification: Rules provide a clear framework for identifying predefined fraud scenarios.
- Swift Action: Real-time application allows immediate action, minimizing potential financial losses.
- Tailored Solutions: Rules can be fine-tuned to suit specific business needs and risks.
Limitations
- Rigidity: The explicitness of rules, while an advantage, can become a limitation, potentially missing novel fraud patterns.
- False Positives: Vigilance may lead to false positives, flagging legitimate transactions as potentially fraudulent.
- Manual Maintenance: Regular updates and manual maintenance of rules are necessary to keep pace with evolving fraud tactics.
In the world of fraud detection, rules-based approaches play a significant role. Their structured nature provides a foundation for risk mitigation. Understanding the intricacies, strengths, and potential pitfalls is crucial for harnessing their full potential. It's a dance of precision and adaptability, where rules serve not just as defenders but as strategists in the battle against financial deceit.
Practical implementation of rules based fraud detection
Let's step onboard with a common fraud scenario: Unauthorized Account Access.
In this scenario, a user's account is accessed by an unauthorized entity. Imagine a user, who typically logs in from her hometown during business hours. Suddenly, the system detects a login attempt from a different country at an unusual time, say midnight. This unauthorized access raises concerns as it deviates significantly from the user's usual login behavior.
Impact on Organization:
- Financial Loss: If unauthorized access leads to fund transfers or account misuse.
- Reputational Damage: Customer trust may decline due to perceived insecurity.
- Legal Consequences: Regulatory fines may be incurred for failing to secure customer information.
To illustrate the effectiveness of Nected's rules-based approach, let's explore how it could handle the scenario:
Context: An account typically accessed from a specific region suddenly logs in from an unusual location at an odd hour.
Rule Implementation: Create a rule in Nected specifying conditions like login location and time. Any deviation triggers the rule.
Real-time Detection: Nected detects the unusual login attempt in real-time.
Alert Generation: An alert is generated immediately, notifying administrators of the suspicious login activity.
Automated Response: Configure rule engine to implement precautionary measures, such as temporarily locking the account and sending an account verification email.
In this exploration, we've laid out a hypothetical scenario of unauthorized account access, discussed the potential impact on an organization, and elucidated the importance of Nected's rules-based approach in swiftly detecting and mitigating such fraudulent activities.
Now let us move to the real implementation of rules based fraud detection using Nected.
Quick Implementation Guide
Scenario: Unauthorized Account Access
Open your web browser and navigate to the Nected platform. Log in with your credentials.
Step 1: Creating a New Rule
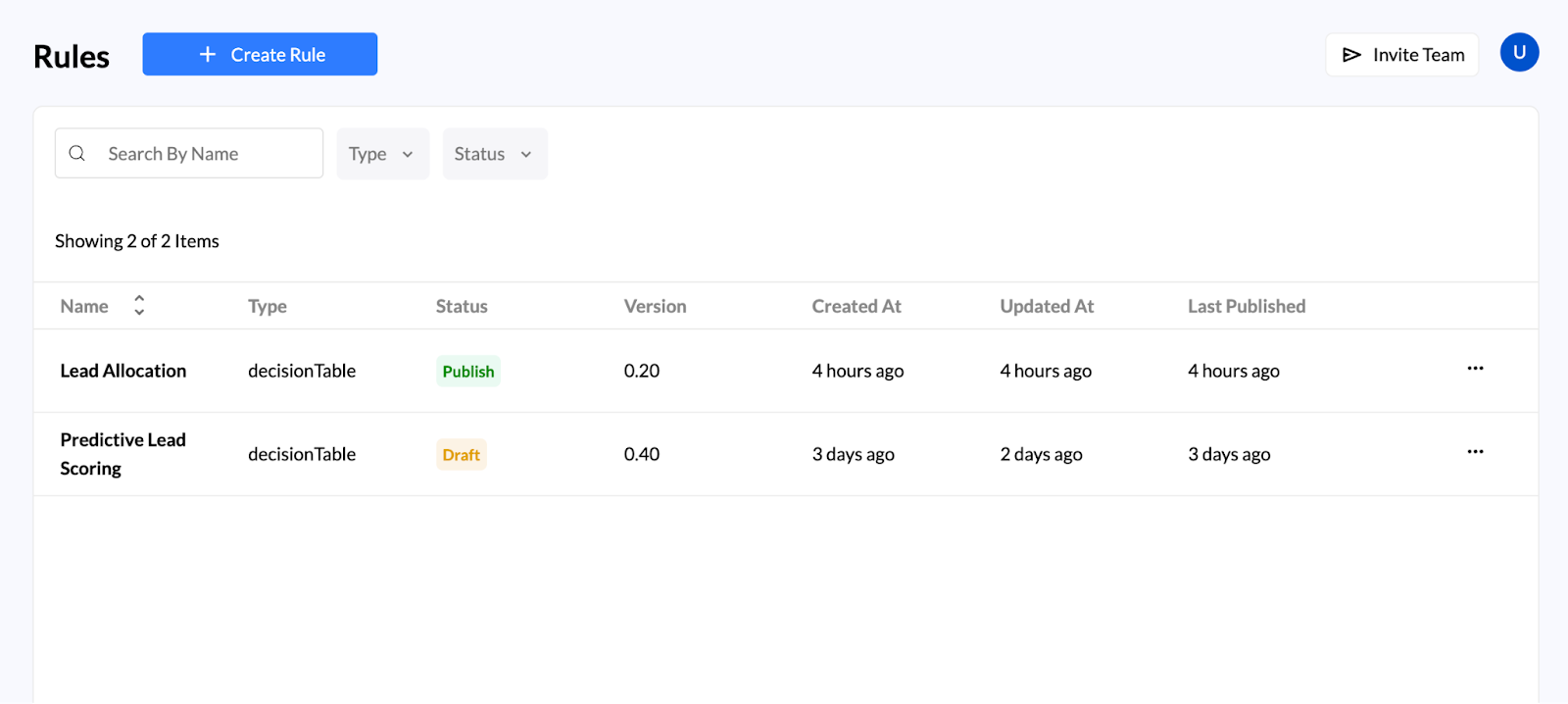
In the dashboard, locate and click on the "Rules" section.
Choose the option to "Create New Rule."
Title your rule as "Unauthorized Account Access Detection." Add a description.
Step 2: Defining Conditions for Suspicious Behavior
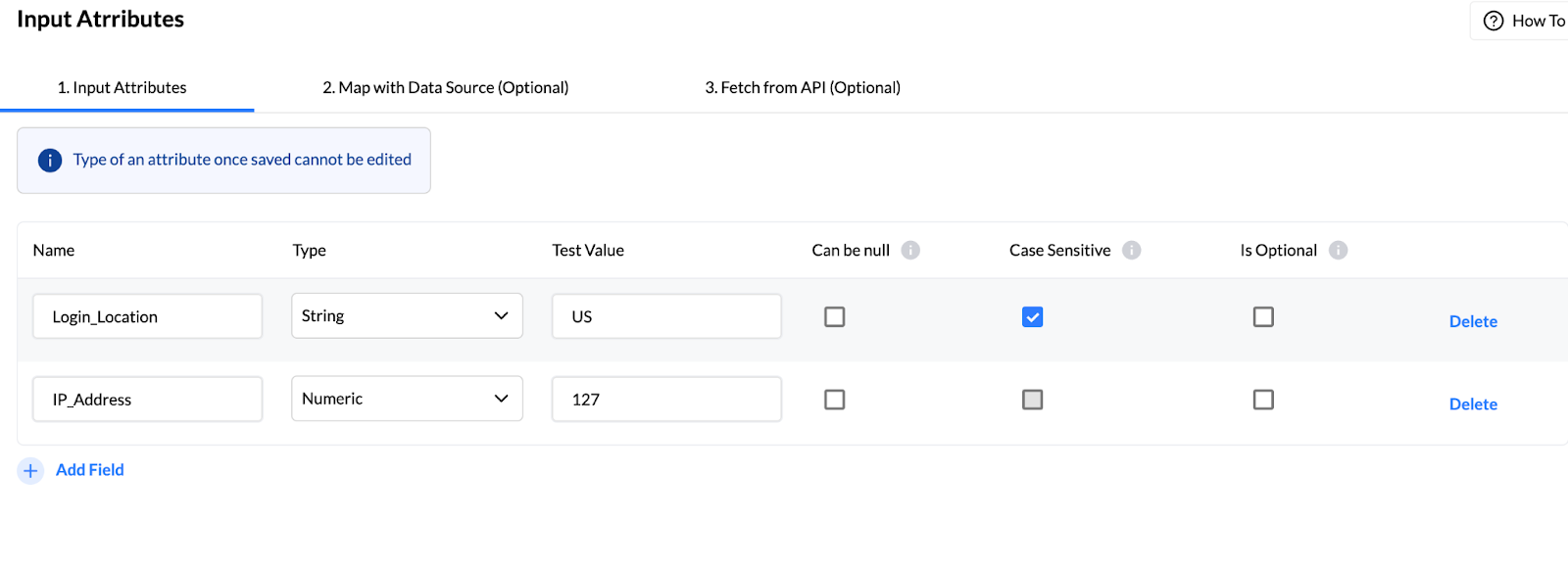
Specify conditions to identify unauthorized access (e.g., multiple logins from different locations).
Utilize Nected's rule creation interface to set criteria based on login history, geography, and time.
Step 3: Configuring Real-time Monitoring
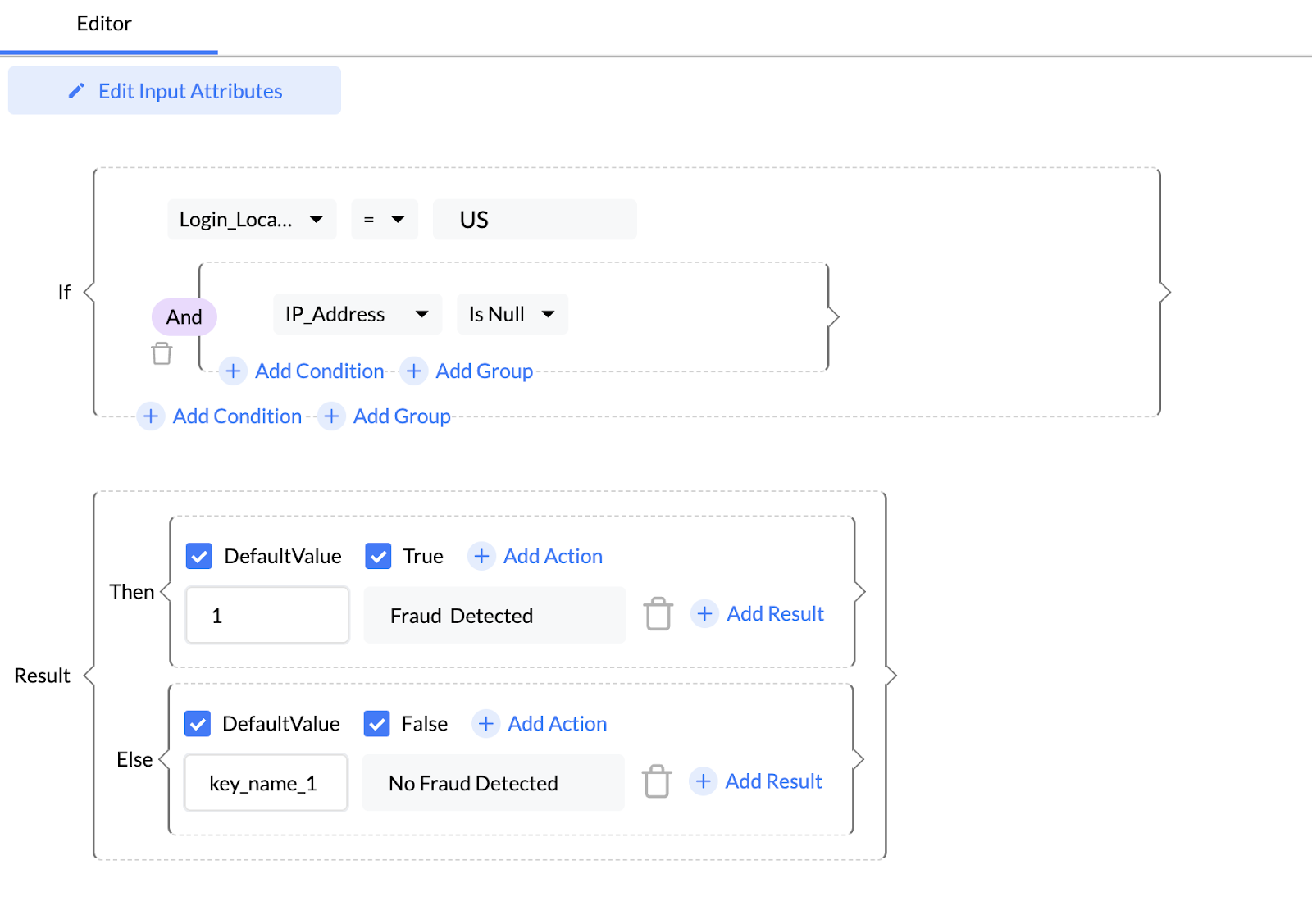
Enable real-time monitoring to ensure instant rule application.
Nected's efficient architecture ensures swift execution without system delays.
Step 4: Setting Up Alert Mechanism
Implement an alert system to notify administrators when the rule is triggered.
Configure alerts through email or preferred communication channels.
Step 5: Automated Response Setup
Establish an automated response plan (e.g., temporary account lock or additional verification).
Leverage Nected's automation capabilities for seamless execution.
Step 6: Testing in a Controlled Environment
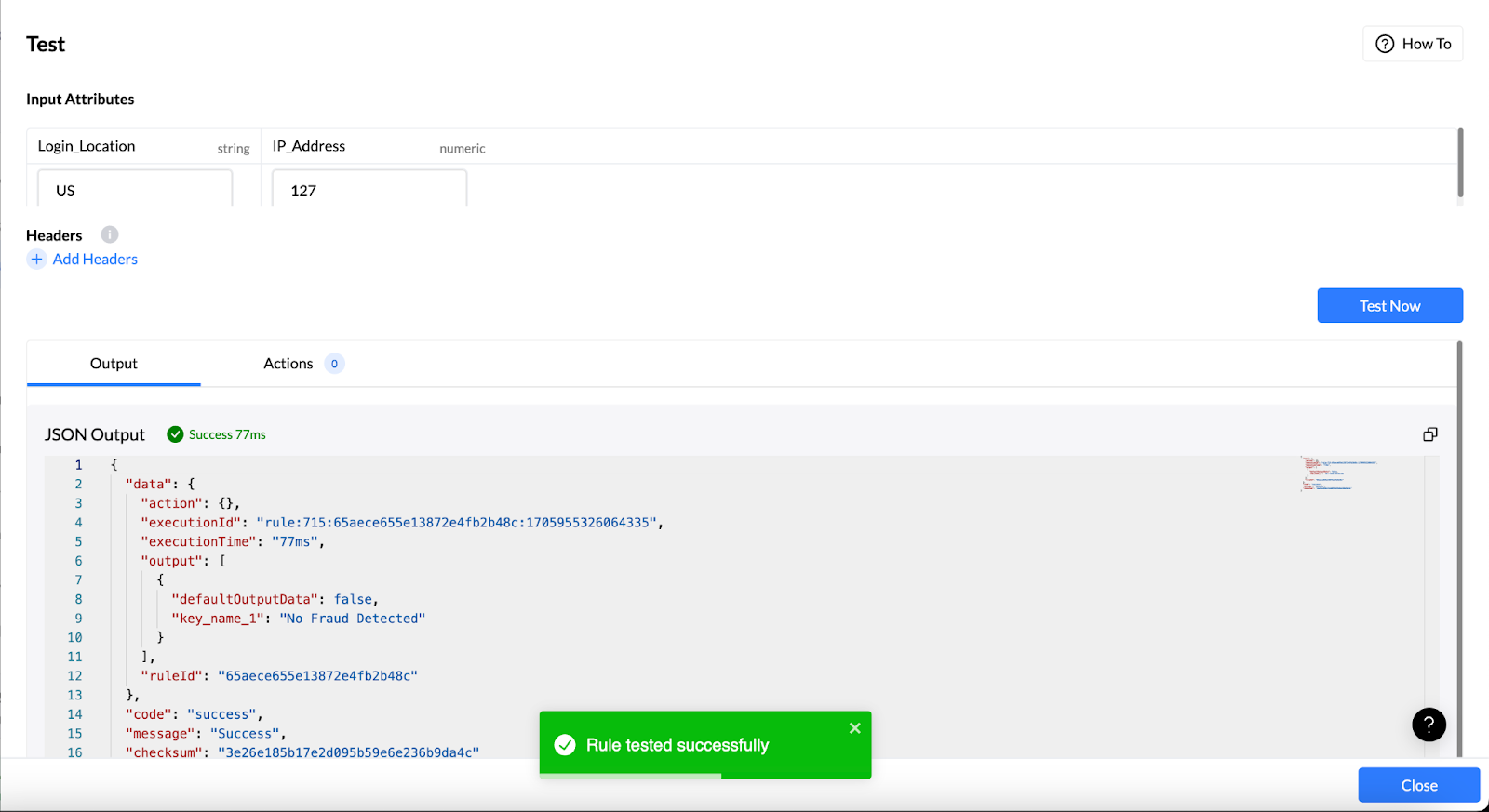
Use Nected's dedicated testing environment to simulate scenarios and ensure the rule's effectiveness.
Validate the rule without impacting real user accounts.
Step 7: Deployment and Continuous Monitoring
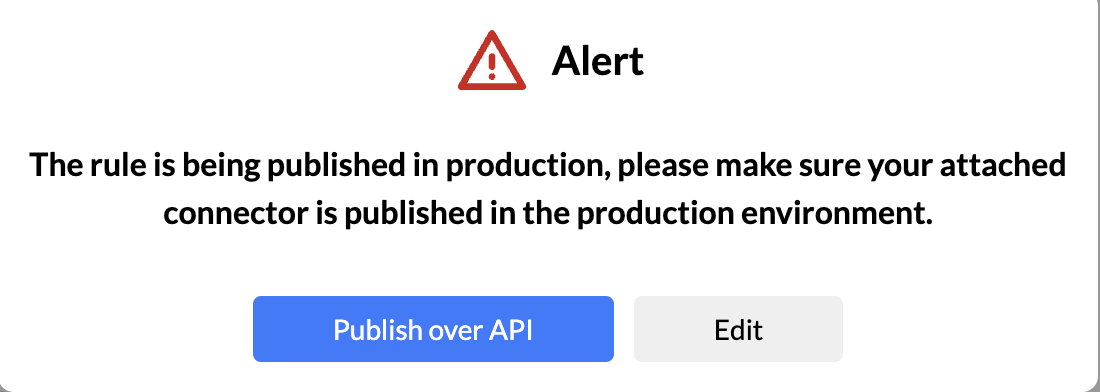
Once satisfied with testing, deploy the rule to the live production environment.
Monitor the rule continuously, making adjustments based on real-time insights.
Step 8: Regular Review and Update
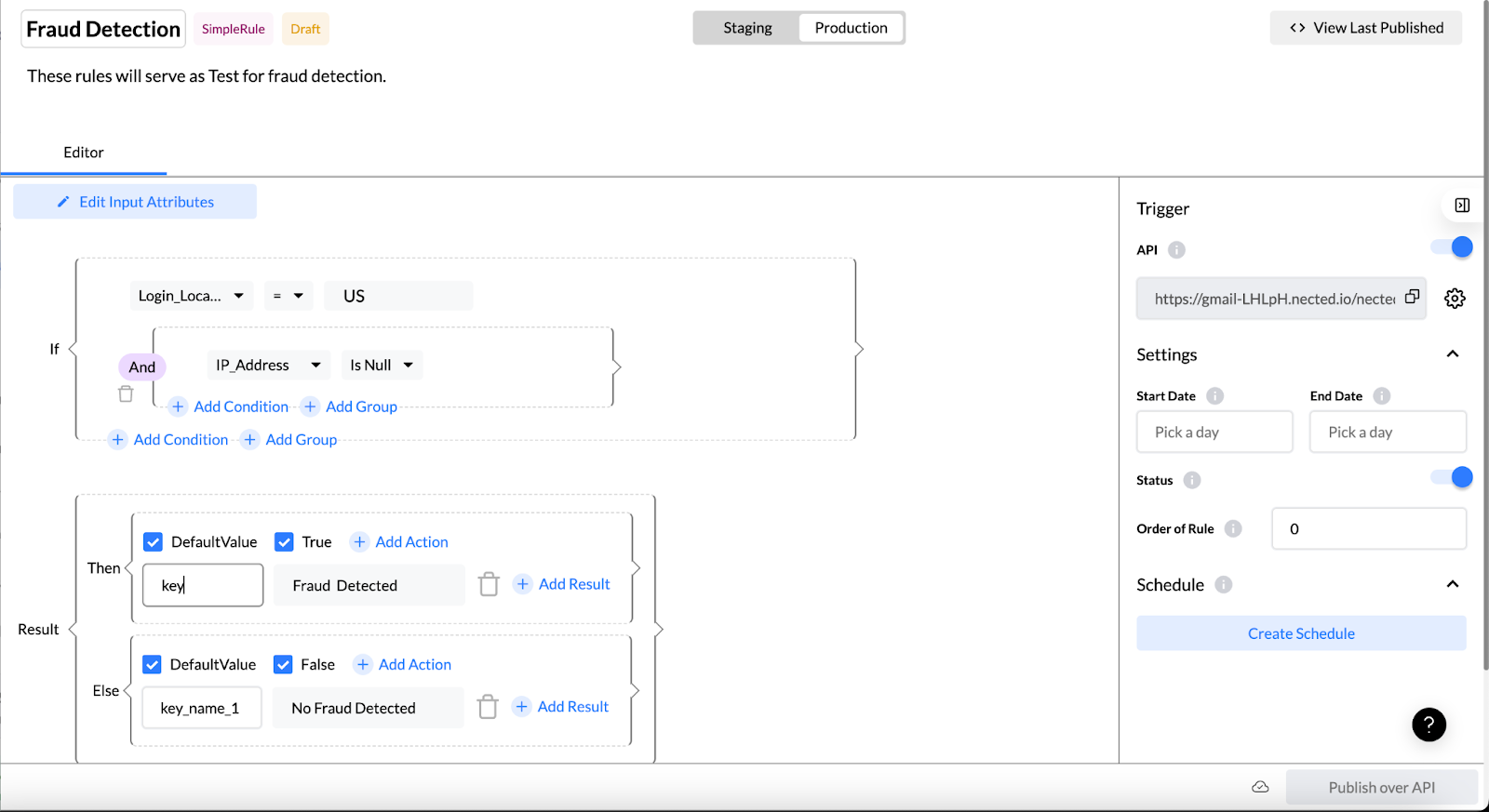
Periodically review and update the rule to adapt to evolving fraud patterns.
Nected's user-friendly interface allows easy modifications for ongoing effectiveness.
This step-by-step guide provides a comprehensive overview of implementing rules-based fraud detection using Nected. From rule creation to deployment and continuous monitoring, Nected streamlines the process for enhanced security measures in organizations.
Nected's rules-based fraud detection system can be useful in various sectors. In finance, it ensures secure transactions and monitors account access. E-commerce platforms benefit from the identification of fraudulent orders and prevention of payment fraud. Healthcare can leverage Nected for safeguarding patient data and detecting fraudulent insurance claims. Telecommunications can rely on it to monitor network activities and combat SIM card fraud. Government agencies securing sensitive data, online gaming platforms detecting suspicious activities, supply chain optimization, and educational institutions ensuring integrity—all these sectors can make use of Nected's adaptable solutions, making it a practical tool in the fight against fraud.
Choosing Nected for Rules-Based Fraud Detection:

When it comes to selecting a system for rules-based fraud detection, Nected stands out for several reasons. Its features are tailored to meet the complex demands of fraud detection efficiently.
1. Flexibility:
Nected offers a high degree of flexibility in crafting and modifying rules. This adaptability ensures that businesses can stay ahead of evolving fraud tactics, adjusting detection strategies in real-time.
2. Scalability:
Scalability is crucial in fraud detection, considering the dynamic nature of fraudulent activities. Nected's architecture allows seamless scalability, accommodating increasing data volumes and expanding detection requirements.
3. Ease of Implementation:
Implementing a fraud detection system can be a daunting task, but Nected simplifies this process. Its user-friendly interface and comprehensive documentation make it accessible even for those without extensive technical backgrounds.
4. Advanced Tools and Functionalities:
Within Nected, the arsenal for rules-based fraud detection is equipped with a spectrum of advanced tools and functionalities, making it a formidable choice in fortifying an organization against fraudulent activities.
Nected allows the formulation of straightforward rules that can be easily crafted and modified. These rules are the backbone of the fraud detection system, providing a simple yet powerful mechanism to catch irregularities in transactions or user behavior.
The use of decision tables in Nected adds a layer of sophistication to the fraud detection process. These tables allow for a structured approach, enabling businesses to make nuanced decisions based on a variety of conditions and outcomes.
Nected's implementation of rule sets adds a layer of complexity and adaptability. Rule sets enable businesses to organize and manage rules efficiently, allowing for a more systematic and refined approach to fraud detection.
5. Real-time Monitoring:
Nected's real-time monitoring feature is like having a vigilant sentry at the gate. It actively observes incoming data and transactions, swiftly identifying potential fraud as it happens.
Choosing Nected for rules-based fraud detection ensures not just a reliable system but an adaptive and scalable solution that aligns with the unique needs of each business.
Building In-House vs. Buying a rule Engine
When considering the implementation of a rules-based fraud detection system, the choice between building an in-house solution or leveraging Nected involves various technical aspects and challenges.
Building In-House:
- Developing an in-house system demands a significant investment of time and expertise. Crafting an effective set of rules, implementing real-time monitoring, and ensuring scalability are substantial technical challenges.
- Building an in-house system often requires a dedicated team of developers, data scientists, and cybersecurity experts. This can lead to a strain on internal resources.
Using Nected:
- Nected offers a rapid implementation process. With its user-friendly interface, businesses can swiftly configure rules, decision tables, and rule sets without an extensive learning curve.
- Nected's cloud-based architecture ensures scalability. As the volume of data and transactions increases, the system effortlessly accommodates the growing demands without compromising efficiency.
- Opting for Nected can be more cost-effective than investing in an in-house solution. The subscription model and the avoidance of upfront development costs contribute to a more predictable financial model.
Conclusion
In wrapping up our exploration into the domain of rules-based fraud detection, it becomes evident that safeguarding businesses against fraudulent activities is not merely a necessity but a strategic imperative. The implementation of robust fraud detection mechanisms is of supreme importance, and the choice between in-house development and leveraging cutting-edge solutions like Nected plays a pivotal role.
We've journeyed through the significance of fraud detection, the various types of fraud, and the merits of a rules-based approach. The rules-based fraud detection landscape is dynamic, and Nected, with its advanced tools and functionalities, emerges as a beacon in this space.
Nected streamlines the complex process of fraud detection by offering a user-friendly interface for crafting rules, decision tables, and rule sets. Its real-time monitoring capabilities and detailed reporting further empower businesses to stay one step ahead of potential threats.
As we deliberate on the decision to build an in-house solution or opt for Nected, the technical advantages, quick implementation, scalability, and cost-effectiveness of Nected shine through. The choice is not merely between systems but a strategic decision impacting the resilience and future-readiness of an organization.
In conclusion, the blog has endeavored to demystify the intricate landscape of rules-based fraud detection, highlighting the role of Nected as a catalyst for efficient, scalable, and cost-effective fraud prevention. As businesses navigate the complexities of security, Nected stands as a reliable ally, ensuring that organizations can fortify themselves against fraud while maintaining operational agility and efficiency. In the dynamic world of cybersecurity, Nected serves as a beacon, illuminating the path towards a secure and resilient future.

FAQs
Q1. What is a rules-based system?
A rules-based system is a type of decision-making framework that operates on predefined logic or conditions, allowing automated responses based on specified rules.
Q2. How does a rules-based fraud detection system work?
A rules-based fraud detection system relies on predefined rules and conditions to identify patterns indicative of fraudulent activities, ensuring timely detection and prevention.
Q3. Why choose Nected for rules-based fraud detection?
Nected excels in rules-based fraud detection by offering a user-friendly interface for crafting rules, decision tables, and rule sets. Its advanced tools and real-time monitoring capabilities make it a reliable choice for efficient and effective fraud prevention.
.svg%20(1).webp)


.svg)



.png)




.webp)

.svg)





.webp)




